I've got a new NEO which i want to use as a smartcard for Bitlocker on windows 7 64bit. Following a Microsoft guide on certificate creation using certreq.exe i've tried to create a certificate with the following parameter file:
[NewRequest]
Subject = "CN=BitLocker"
KeyLength = 2048
ProviderName = "Microsoft Smart Card Key Storage Provider"
KeySpec = "AT_KEYEXCHANGE"
KeyUsage = "CERT_KEY_ENCIPHERMENT_KEY_USAGE"
KeyUsageProperty = "NCRYPT_ALLOW_DECRYPT_FLAG"
RequestType = Cert
SMIME = FALSE
[EnhancedKeyUsageExtension]
OID=1.3.6.1.4.1.311.67.1.1
From here:
https://technet.microsoft.com/en-us/library/dd875530(v=ws.10).aspx#BKMK_sscertBut when i do that, it prompts me to insert a smartcard, even though the NEO is plugged in, and the PIV manager can see it.
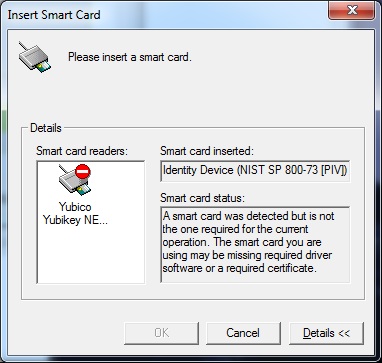
CCID is enabled on the NEO, Windows control panel shows the smart card reader installed as a "Microsoft Usbccid Smartcard Reader (WUDF)", and shows the smart card installed as an "identity Device (NIST SP 800-73 [PIV])", both of which as far as i can tell from reading documentation are correct.
Attachment:
 card.jpg [ 45 KiB | Viewed 5990 times ]
card.jpg [ 45 KiB | Viewed 5990 times ]
But i get a prompt saying: "A smart card was detected but is not the one required for the current operation. The smart card you are using may be missing required driver software or a required certificate". This box shows the NEO as the reader and the correct identity device.
Am i missing something?
If i instead use the Yubikey PIV manager (1.0.2), click certificates, and click generate new key. Select a 2048bit self signed certificate, enter PIN and management key, it generates a new key in slot 91, and loads a self signed certificate. But if I then go to a bitlocker protected volume and try to use the smartcard, it says a certificate suitable for Bitlocker cannot be found on my smartcard.
Ive been through various guides, but cant find a solution.
Am i missing something?
Thanks.









